Did you know
Obsession with the yellow metal…GOLD
CASL vs. GDPR
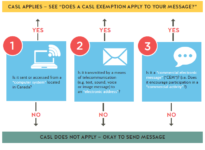
Canada’s anti-spam legislation (CASL) is the federal law dealing with spam and other electronic threats. It is meant to protect Canadians while ensuring that businesses can continue to compete in the global marketplace CASL is a new anti-spam law that will apply to all electronic messages (i.e. email, texts) organizations send…
FIVE steps to keeping your tablets and phones

Smart phones and tablets needs more protection than desktops Switch on PIN/password protection/fingerprint recognition for mobile devices Configure devices so that when lost or stolen they can be tracked, remotely wiped or remotely locked Keep your devices and apps installed up to date using the automatically update option When sending…
Happy New Year 2019
What is Whaling?

Whaling is a specific kind of phishing targeted at high-ranking bankers, executives or others in powerful positions or job titles. This highly targeted phishing attacks (masquerading as legitimate emails) that are aimed at senior executives. Those who are engaged in whaling may, for example, hack into specific networks where these…
World of DevOps
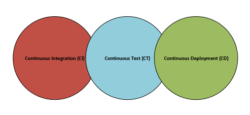
Definition DevOps is a term used to refer to a set of practices that emphasize the collaboration and communication of both software developers and information technology professionals while automating the process of software delivery and infrastructure changes. DevOps emerged from an effort by businesses to respond more rapidly to market…
A product recall may hurt its rival too – a phenomenon called perverse halo
When is a technology matured?

For the new technology, the key factor is how quickly its ecosystem becomes sufficiently developed for users to realize the technology’s potential.In the case of cloud-based applications and storage, for example, success depended not just on figuring out how to manage data in server farms, but also on ensuring the…







